Security problem in web cameras sold by CNB Technology
Posted by Javi Lavandeira in Computer Security, Internet | May 10, 2013A few days ago I noticed that I was receiving weird HTTP requests on my frontend web server. The requests were addressed to a domain that doesn’t exists in any of my servers, so initially I thought it was some kind of attack. Out of curiosity I decided to investigate a bit, and it turned out to be something way more interesting.
The requests looked like this:
61.125.xxx.xxx - - [05/May/2013:00:33:38 +0900] "POST http://autoipset.com/ddns/UpdateHost.php HTTP/1.0" 200 3 "-" "-" 61.125.xxx.xxx - - [05/May/2013:00:43:38 +0900] "POST http://autoipset.com/ddns/UpdateHost.php HTTP/1.0" 200 3 "-" "-" 122.19.xxx.xxx - - [05/May/2013:00:45:46 +0900] "POST http://autoipset.com/ddns/RegisterHost.php HTTP/1.0" 200 3 "-" "-" 180.31.xxx.xxx - - [05/May/2013:00:47:53 +0900] "POST http://autoipset.com/ddns/RegisterHost.php HTTP/1.0" 200 3 "-" "-" 114.166.xxx.xxx - - [05/May/2013:00:54:57 +0900] "POST http://autoipset.com/ddns/UpdateHost.php HTTP/1.0" 200 3 "-" "-" 61.125.xxx.xxx - - [05/May/2013:02:03:48 +0900] "POST http://autoipset.com/ddns/UpdateHost.php HTTP/1.0" 200 3 "-" "-" 180.31.xxx.xxx - - [05/May/2013:02:13:05 +0900] "POST http://autoipset.com/ddns/UpdateHost.php HTTP/1.0" 200 3 "-" "-"
(These logs show an HTTP status code of 200 instead of 404 because this is after changing some things on my server. Keep reading for details.)
In other words, several machines from a bunch of different dynamic IP addresses were sending data via HTTP POST to a couple of PHP scripts (/ddns/UpdateHost.php and /ddns/RegisterHost.php) in the autoipset.com domain.
What puzzled me is that autoipset.com is not, and has never been, hosted in any of my servers.
Keep reading to see the rest of the story…
The autoipset.com domain
The first thing I did was check whether autoipset.com actually exists, who owns it, and what appears when we enter via web.
[javilm]MacBook-Pro:~ $ whois autoipset.com [...] Domain Name: AUTOIPSET.COM Registrar: JUNGBONET CO LTD Whois Server: whois.jungbo.net Referral URL: http://www.jungbo.net Name Server: NS1.AUTOIPSET.COM Status: ok Updated Date: 2011-04-07 Creation Date: 2007-06-27 Expiration Date: 2013-06-27 Registrant: Seung Hyo, Kim, whitecity@cnbtec.com Gumcheon-Gu,Seoul,Korea #701,Star Valley ,60-11 Gasan-Don SEOUL, SEOUL 153-801 KR [...]
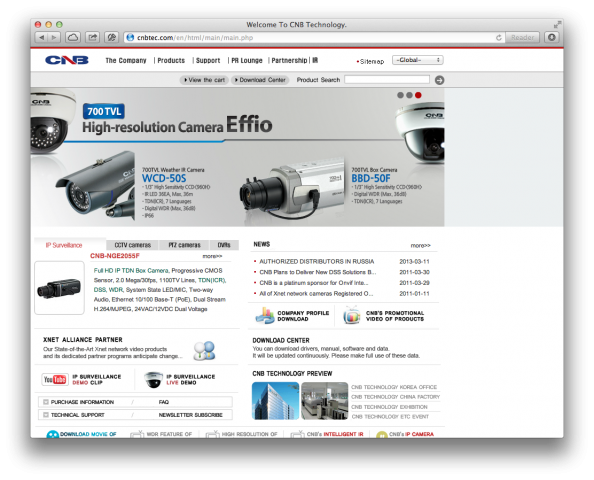
The domain exists, and it belongs to a South Korean company called CNB Technology. Apparently they sell surveillance cameras with Internet connectivity:
The autoipset.com domain appears to be a dynamic DNS service offered by this company:
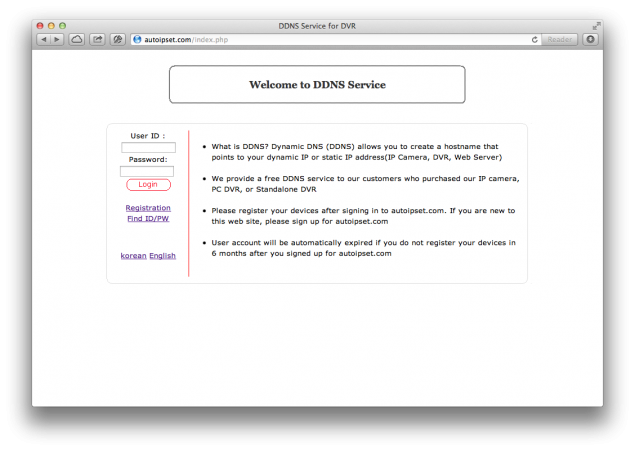
All of this looks a bit weird, but it doesn’t seem to be an attack. I’m guessing that the cameras sold by CNB Technology use this dynamic DNS service that allows the customer to access the video streams from anywhere using just a web browser.
However, why are the cameras sending those requests to my server? I don’t have anything to do with this Korean company!
Gathering data
In order to find out what was going on, I needed to know what parameters the cameras were sending me. I configured my web server to reply to requests addressed to the autoipset.com domain, and I wrote a small PHP script to send me via email all the data received on the HTTP request:
<?
$mail_body = "POST PARAMETERS\n";
$mail_body .= "===============\n\n";
foreach ($_POST as $key => $value) {
$mail_body .= "$key : $value\n";
}
$mail_body .= "\n\n";
$mail_body .= "SERVER PARAMETERS\n";
$mail_body .= "=================\n\n";
foreach ($_SERVER as $key => $value) {
$mail_body .= "$key : $value\n";
}
$recipient = 'javi@lavandeira.net';
$subject = '[autoipset vhost] POST DATA';
$header = 'From: autoipset vhost <autoipset@lavandeira.net>';
mail($recipient, $subject, $mail_body, $header);
?>
Ok
This script captures all the parameters sent via HTTP POST and all the environment variables seen by the web process (such as the URL used to post the data, the remote IP address, etc), and sends them to me via email. Once the script was online, the only thing I could do was wait, so I went to sleep.
Analyzing the data
The next morning I found several mails sent by the script. There were two different formats: one for requests sent to RegisterHost.php and another for the ones sent to UpdateHost.php.
RegisterHost receives parameters in this format:
INFO : 00220E03A600::xxxxxxxx::zzzzzzzz::B59C67BF196A4758191E42F76670CEBA::autoipset.com.::192.168.11.240::1.5.2::2::ED04::81::10104::
I redacted xxxxxxxx and zzzzzzzz because these fields contain sensitive information. My guesses for the meaning of these fields:
- 00220E03A600 is the MAC address of the Ethernet interface on the camera. The maker is Indigo Security Co., Ltd.
- xxxxxxxx is a subdomain name for the dynamic DNS service.
- zzzzzzzz is the autoipset.com user ID.
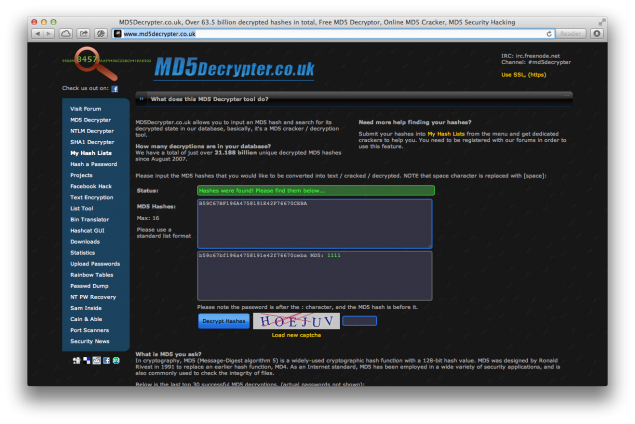
- B59C67BF196A4758191E42F76670CEBA is the MD5 hash of the user’s password.
- 192.168.11.240 is the private IP address of the camera.
- 1.5.2 seems to be some kind of version number (software?)
I have no clue about what the other fields may be (ED04, 81 and 10104).
UpdateHost receives the following parameters:
User_id : xxxxxxxx domain : autoipset.com. MacAddress : 00220E03A79E PrivateIP : 192.168.11.50
All of them are obvious thanks to the variable names. Again, I’ve redacted the user ID.
The camera’s web interface
Opening the URL posted to RegisterHost.php (http://xxxxxxxx.autoipset.com) I see this:
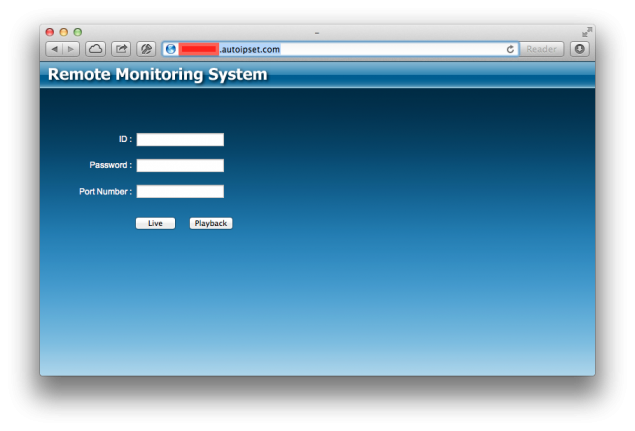
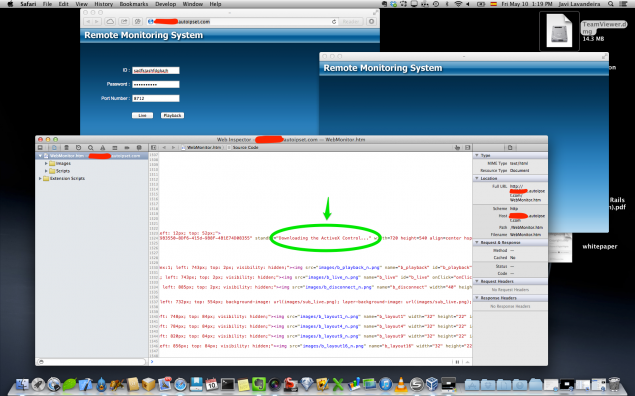
If I try and login with a random ID and password I get a blank popup window saying “Remote Monitoring System”, but looking at the source code I see that the problem is that it requires an Internet Explorer plugin, which won’t run on my OS X system:
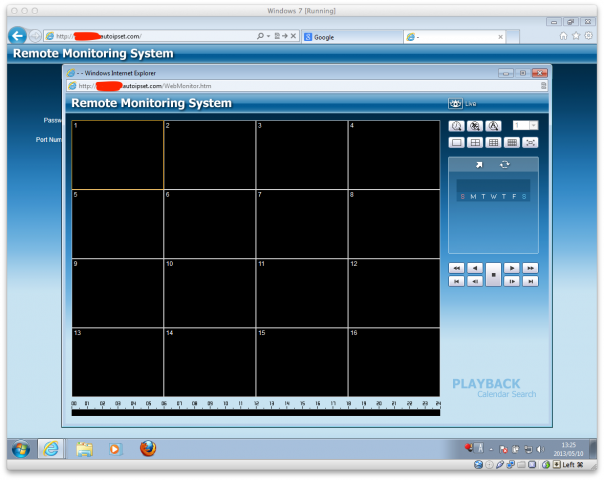
It run just fine in a Windows 7 virtual machine, though the video streams don’t work. I assume this is because I didn’t log in with the right user ID and password:
Conclusion
After all we’ve seen, my impression is that the cameras sold by CNB Technology have a serious security problem. Since they are sending all these parameters to my server, we have to assume that they’re also sending these to other servers on the Internet. Probably someone is already exploiting this to access these cameras.
It is true that the password isn’t sent as plaintext, but recovering a password from an MD5 hash is very often trivial if we used precomputed hash tables:
If you own one of these cameras, my advice is that you disable the dynamic DNS service to keep them from sending your details to random servers on the Internet.
I’ve tried getting in touch with CNB Technology, but so far I haven’t received any reply from them.